[et_pb_section fb_built=”1″ module_id=”aboutus” _builder_version=”3.9″ background_color=”#f5f5f5″ custom_padding=”41px|0px|41px|0px|false|false”][et_pb_row custom_padding=”7px|0px|10px|0px|false|false” custom_margin=”41px|||” _builder_version=”3.9″][et_pb_column type=”4_4″ _builder_version=”3.0.47″ parallax=”off” parallax_method=”on”][et_pb_text _builder_version=”3.9″ header_font=”||||||||” header_text_align=”center” header_text_color=”#161616″ header_line_height=”1.2em” header_2_font=”||||||||” header_2_text_align=”center” header_2_text_color=”#161616″ header_2_font_size=”30px” header_2_line_height=”1.2em” custom_margin=”||10px|”]
Identifying Clock Manipulation or when a Hot Loader was used on an IOS Device
This article is intended to help other experts in the field of digital forensics. It is also intended to help attorneys identify possible fake data or fake evidence produced to the court. *Disclaimer: The identities of all individuals, devices, and the cases used in this article have been redacted.
Over the past three years or so, I have run into cell phone extractions where the system date and time was manipulated after seizure. The types of cases where I’ve seen more than 20 mobile devices with the same similar open source applications or components running the same commands, java scripts, SQL statements, triggers, arguments, etc are as follows:
- Criminal cases such as capital murder, vehicular manslaughter, child exploitation or child pornography, sexual assault, and theft.
- Civil cases mostly car or truck accidents and wrongful death cases in general.
- Divorce cases usually to hide evidence items outside of the agreed timeline and protocol
- Wrongful termination cases where evidence was added to an employee’s workstation (Not a mobile device) well after they had left the
- Commercial Litigation cases and backdating agreements
[/et_pb_text][/et_pb_column][/et_pb_row][et_pb_row custom_padding=”12px|0px|8px|0px|false|false” _builder_version=”3.9″][et_pb_column type=”4_4″ _builder_version=”3.0.47″ parallax=”off” parallax_method=”on”][et_pb_text _builder_version=”3.9″ header_font=”||||||||” header_2_font=”||||||||” header_2_text_align=”center” header_2_text_color=”#161616″ header_2_font_size=”30px” header_2_line_height=”1.2em” custom_margin=”||10px|”]
Tools used
Cellebrite UFED and Physical Analyzer
Exterro (Formally AccessData) Forensic Tool Kit
AccessData FTK Imager (Free version for viewing exported trace logs and other files not parsed by Cellebrite PA if you do not possess a full FTK license)
Digital Detective Dcode 5.5 for converting Unix or MAC absolute timestamps to conventional time.
*You will see the most important keywords from list on backdating a device in general. I actually works for Android devices as well as even computers running the Windows Operating System. My hope is that all experts around the country will pass this information along.
The first case that I noticed clock manipulation was for a criminal case where the cell phone was backdated in order to add google searches to the owner’s device. The anomalies, discrepancies, data inconsistencies, and evidence items that just did not make sense revealed to me an IOS operating system environment where it was flat out impossible to operate that way. I determined that fake data was added to the device to make that person appear to have researched how to commit the crime this person was accused of.
For an explanation to what Unix and MAC Absolute timestamps are and their conversion to conventional date timestamps, refer to this article:
https://library.mosse-institute.com/articles/2022/04/timestamp-format-in-windows-linux-mac-os/timestamp-format-in-windows-linux-mac-os.html
Some of those items we will cover in this article include:
- Code for “React Hot Loader”, “Secret Internals, or “Blueimp”
- Any open-source web kits or dev tools installed after seizure
- Incoming text messages that were forward in time of the extraction date and time in some cases by days or months (In the future)
- Cookies’ timestamps indicating that the creation date is ahead or after the “last visit” date.
- An unusually large number of zero length files or corrupt files with zero bytes due to future dated files being transferred back to a device whose IOS clock is set back to a current date time setting before that file could have been created. Note here that when a new master file table with a new install of the IOS has a date and time setup back to two months ago, certain files that were backed up usually get restored back to the device after reset and clock change.
- Event Backwards errors or events in various log files or database tables
- Errors such as “Invalid date” or “time sync error”
- Fraud alerts or warnings
- Database files with EPOCH timestamps such as 1970 when those particular files installed with the normal operating system bundle do not.
- Multiple rollbacks
- Unknown bundle or log entries showing “isUnknownContainerModule”
- “Remove previous Timestamp” arguments
- Web kits and and Dev Tools installed after seizure
- IMSI catcher logged
- Fake Hash logged
- Invalidation State logged
- USB write failure
- Deep Clone or Cloneable log entries
- Log entries for “inject”, “injected”, or “injection”
At the time of that first case mentioned above, I found these two articles from Cellebrite on backdating IOS devices. Since then, it almost seems like the forensic community is avoiding the subject. I will not:
https://cellebrite.com/en/if-i-could-turn-back-time-a-closer-look-at-ios-time-modifications/
https://cellebrite.com/en/an-easy-way-to-detect-time-manipulation-on-ios-devices/.
Now let’s go over what a “Hot Loader” is designed to do more specifically the source code for these open-source applications downloaded from github then sometimes customized:
REACT HOT LOADER – This particular open source application. You may see log entries for “Unknown bundle” when the Hot Loader is used. “It is a plugin that allows React components to be live reloaded without the loss of state. It works with Webpack and other bundlers that support both Hot Module Replacement (HMR) and Babel plugins”.
Reference: https://gaearon.github.io/react-hot-loader/getstarted/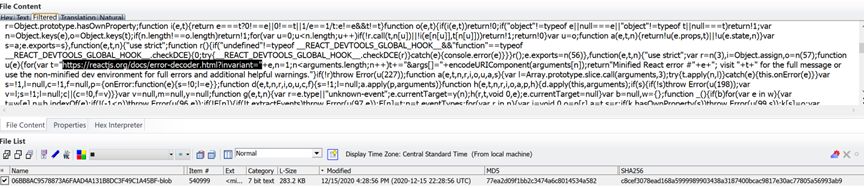
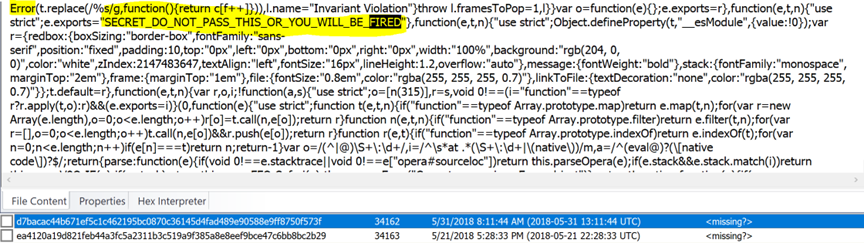
SECRET INTERNALS – You’ll notice that when this open source component was used before an extraction of an iPhone it will usually come with REACT HOT LOADER. You will also see this warning within various java script log files. This warning has been found in four different U.S. states having the exact same warning. Below is a snapshot taken from one of many cases where I’ve noticed these rogue exploit components were installed after seizure and run to setup the device instead of using the normal Apple IOS setup wizard:
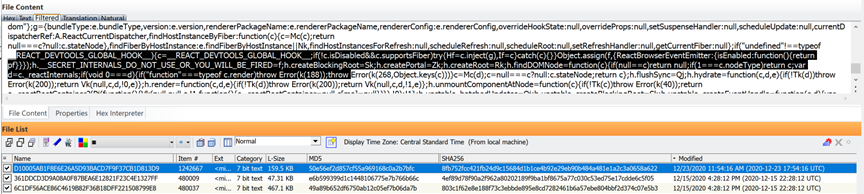
BlueImp – This is another open source application and component of the Hot Loader developed to replace the Apple IOS setup wizard particularly the Time zone date and time setting that comes just before the last option to restore from iCloud or iTunes. The purpose of this component is to give the user the options for setting new timestamps on files restored back to the device after reset.
Whenever you see Blueimp was run while examining the java script log files, you will typically see this disclaimer as pasted from one of the two devices above:
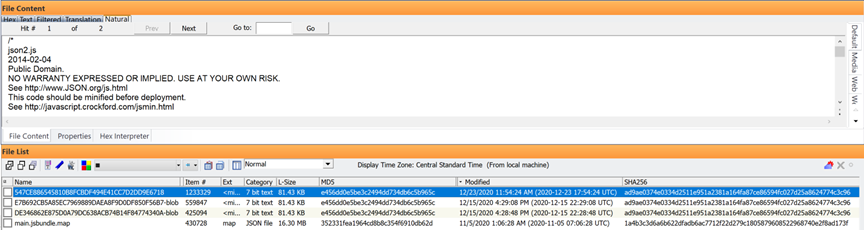
Just below this disclaimer and before the script started, the developers are listed for Blueimp:
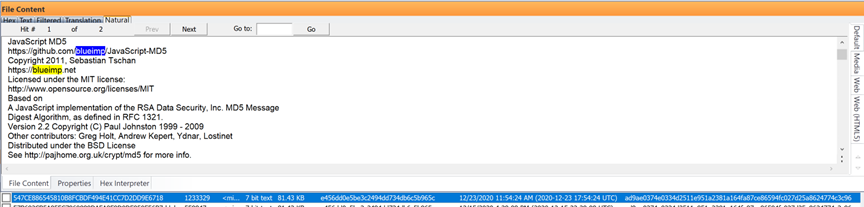
When scrolling down from the disclaimer for the Blueimp open source application with the same java script log file above using the Exterro FTK filter, you can see SQL statements that present an active user selection process of manually setting dates and times on certain files either added back to the device later or during the data transfer process back to the device. Again, this data was generated after seizure in this particular case: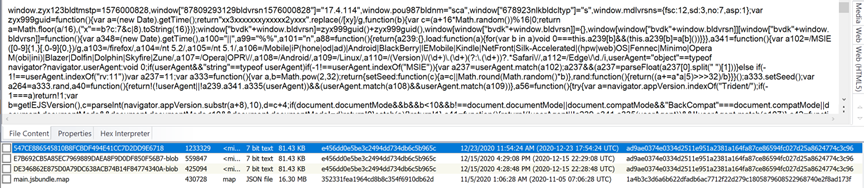
When examining an iPhone extraction to determine possible clock manipulation, my focus is usually on these sqlite databases that come bundled with the IOS on most iPhones. See if you can spot the one 3rd party application that would not qualify:
| Browserstate.db | Unifystorage.sqlite | CallHistory.storedata | Notes.sqlite |
| Store.cloudphotodb | HealthApp.sqlite | Manifest.sqlite | Spinindex.db |
| heimdallr.db* | datastore3.sqlite | TCC.db | ApplicationState.db |
| Datastore3.sqlite | Photos.sqlite | CellularUsage.db | DataUsage.sqlite |
| Data-Local.sqlite | GyroCal.db | History.db | Downloads.sqlitedb |
| Extras.db | History.db | Itunesstored_private.sqlitedb | Kvs.sqlitedb |
| LocalStorage.sqlite3 | Indexdb.sqlite3 | linkd.metadatastore.sqlite3 | managedduplicatestore.sqlite |
| Main.db | medianalysis.db | medialibrary.sqlitedb | observations.db |
| Notestore.db | photosgraph-tmp.kgdb | photosgraph.kgdb | psi.sqlite |
| Server.db | sms.db | syched.db | TrustStore.sqlite3 |
| voicemail.db |
Two things that Apple doesn’t like, and you can tell from the warnings in terms of the IOS security and download failures or install errors. That’s timestamp discrepancies and installing Android APK files. The device typically needs to be jailbroken with Cydia for an Android application to run on an IOS device. Refer to this article which is one of many on the subject:
“Conclusion. Android and iOS are two mutually exclusive mobile OSs, and hence, their apps cannot be run interchangeably. However, there are specific workarounds, with the majority banking on finding the IPA version of the APK file through third-party apps such as emulators, screen mirroring apps, and app installers…..” https://testrigor.com/blog/a-guide-to-using-apk-files-on-ios-devices/#:~:text=Conclusion,mirroring%20apps%2C%20and%20app%20installers.
This is an example from a case I have where you see the iPhone has been taken out of airplane mode after seizure, and there was a failed attempt at downloading and installing an Android APK file as opposed to the typical IOS .IPA file (IPA is the extension for the IOS App Store package file used to distribute applications on IOS).
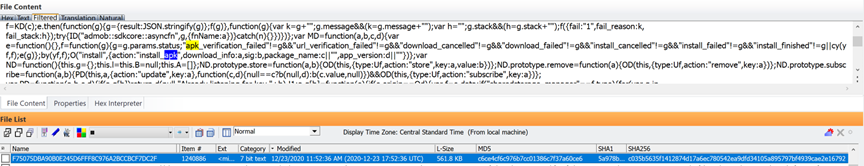
With Exterro FTK, all data is indexed into PostgreSQL database files that allows for superfast queries. In this example from the same device, I ran the Boolean search “unknown w/3 APK” to find this result in one of the many tracev3 log files:
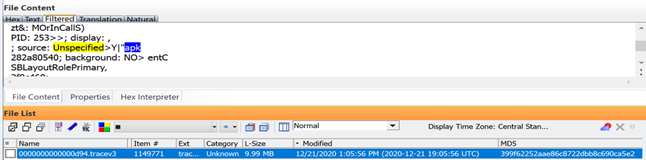
One of the many other reasons I prefer to first examine a Cellebrite extraction through FTK instead of Physical Analyzer is this. The SQLite filter for FTK when viewing a database file always cuts to the chase. You will immediately see how that file was generated and appended in sequence along with its tables, procedures, triggers, and what arguments were executed. In this example, we will see how those SQL statements are run through a normal IOS setup on an iPhone. This is what the SQL procedures looks like when you have the Apple setup wizard running the install of the operating system for the first time or after factory reset option 2.
The test iPhone below is also an iPhone 8 plus. Here we have the database file named “Extras.db” getting created by the actual Apple operating system. Notice there is a time zone selected and set during the typical setup wizard procedure when the user cannot skip this step:
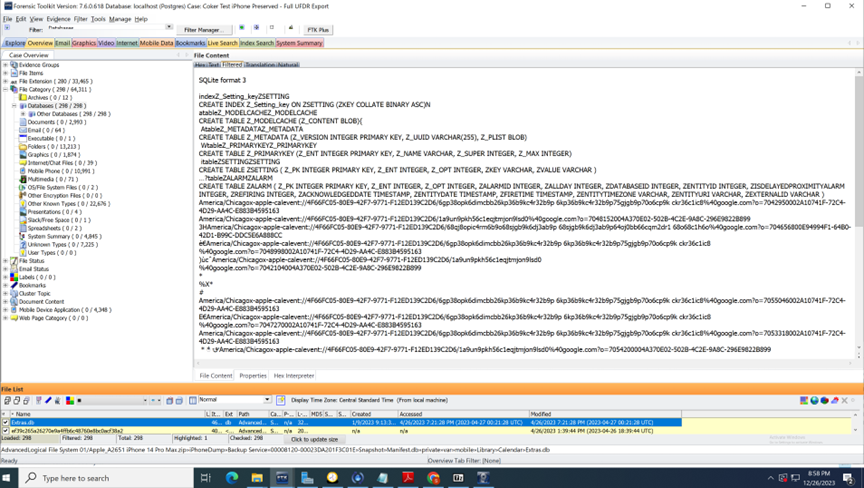
This is the same database created on the same model phone but from an iPhone that has been hijacked. This time it’s a 3rd party exploit application handling the IOS install along with other rogue open-source applications or components The Hot loader is able to get through the setup of this application’s database without the time zone selection usually required by the Apple IOS setup wizard where there is normally no option to skip this selection from the user making those choices after reset most likely because of being jailbroken:
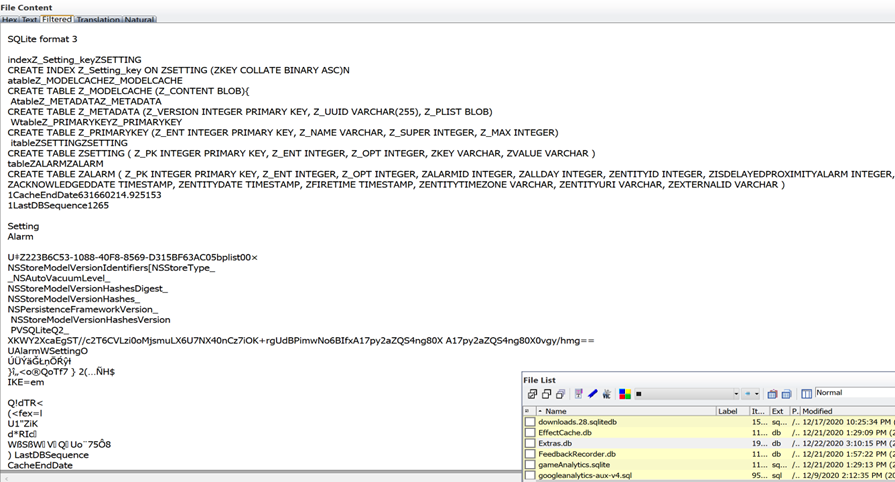
This is the Photos.sqlite database file from my test iPhone is using the normal com.apple.springboardCGIimagePro component when the database is created using the Apple IOS setup wizard.
Page down to table creation in the same database above:

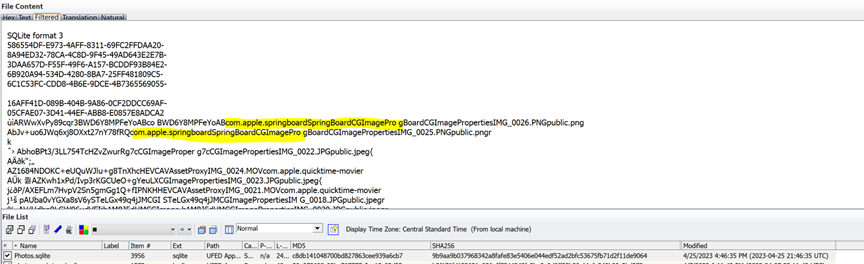
This screenshot of the Photos.sqlite database file from the same extraction above indicates a completely different image editor not seen in the Photos.sqlite database normally installed with the Apple IOS setup wizard. Instead of Springboard CGI Image Pro, you have “Photovision” from a rogue Apple development kit that is being run on this device due to the hot loader running the install of the operating system. Notice that it is also coming from the URL http://www.w3.org/1999/02/22-rdf-syntax-ns# where other open source software and code comes from.
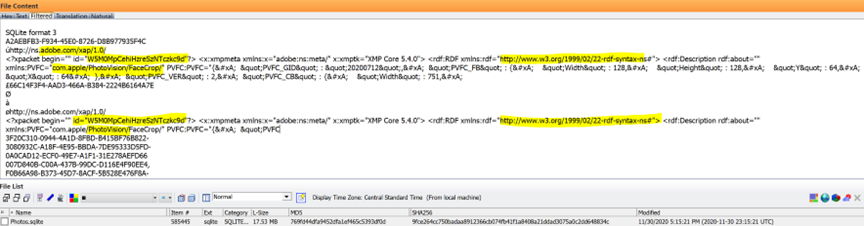
When searching the identifier for this project which is also listed below as “W5M0MpCehiHzreSzNTczkc9d” this is what you get:
https://www.hackerfactor.com/blog/index.php?/archives/552-Deep-Dive.html
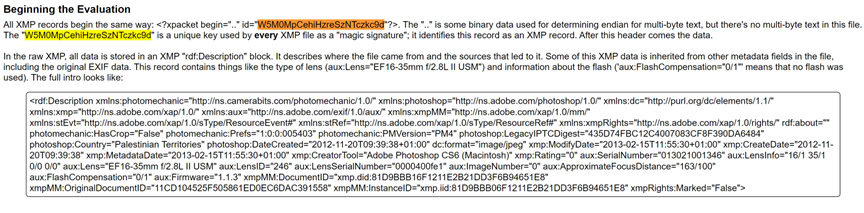
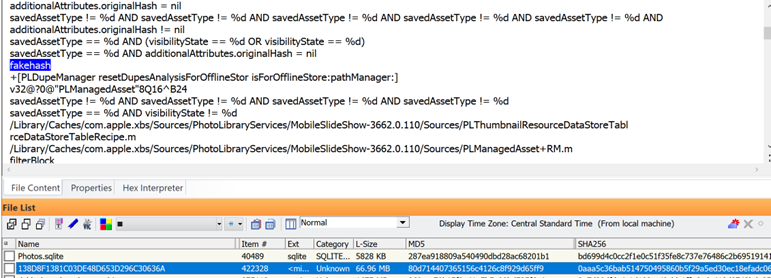
When you page down in the same Photos.sqlite database on the corrupted iPhone, you start to see photos that either index into the database with “FakeHash” because the timestamps are fake or “unknown origin”:
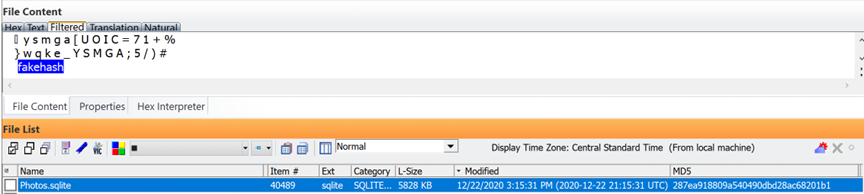
Page down in the same database:
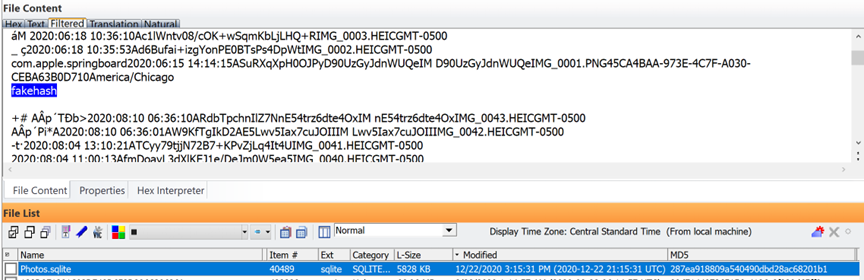
This is a java script log file from the same device above with source code for transferring fake hash photos back to the device:
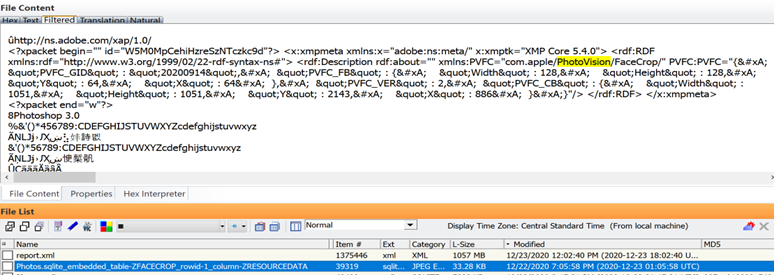
This is the backend code including metadata for one of the images transferred back to the same above device after seizure. Notice it matches:
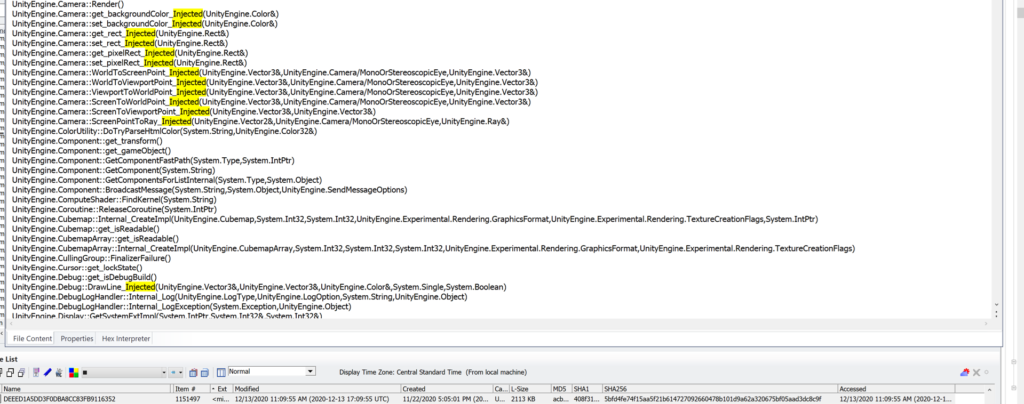
For the devices we’ve covered above, the same Developer tools for “React Hot Loader” and “Secret Internals” is seen with “inject” code:
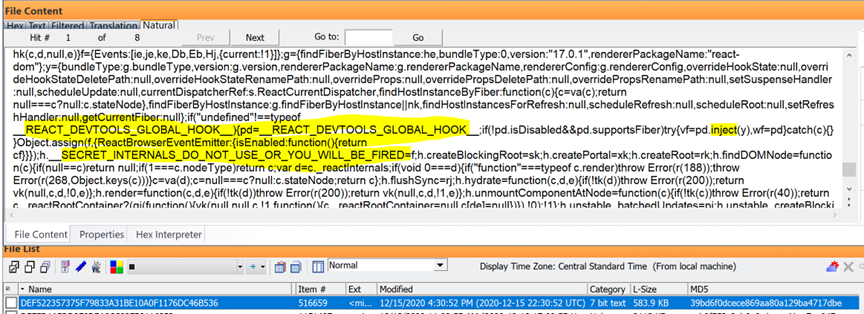
Then scroll down in the same file and there’s errors:
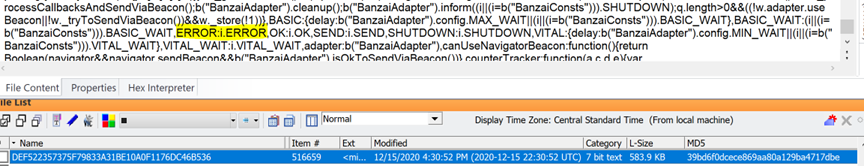
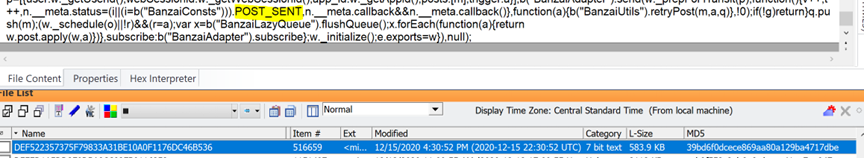
Finally, when you scroll down to the bottom of the same file above, you see “Post Sent”
Here is the same Dev Tools for “React Hot Loader” running on the second phone after seizure:
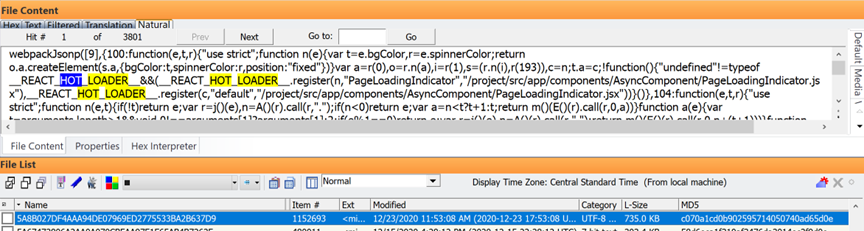
Here is the end of that same file above: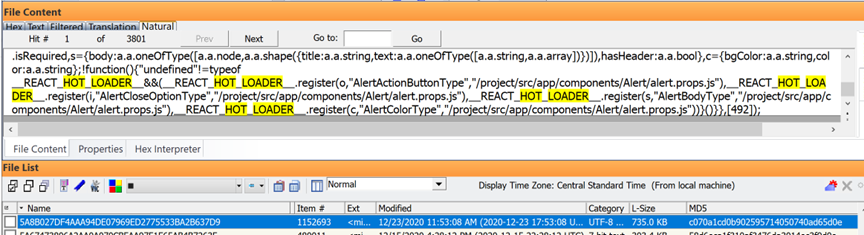
This java script log file shows and effort to inject new data into the same device above after seizure using an IOS SDK (Software developer kit)
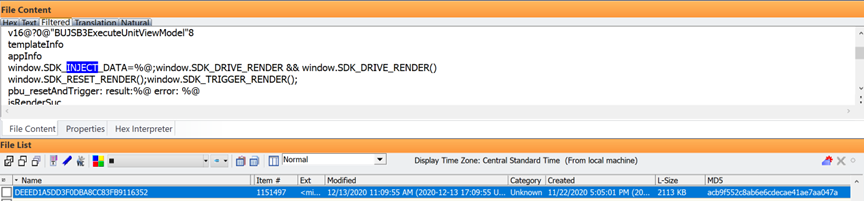
Some of the same processes from the above failed with this error below after using a component “VunglePlayOptionsProvider”
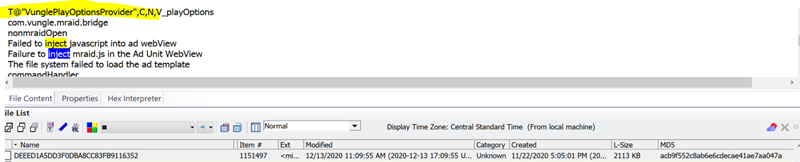
The same file tells the user in plain English that this is illegal:
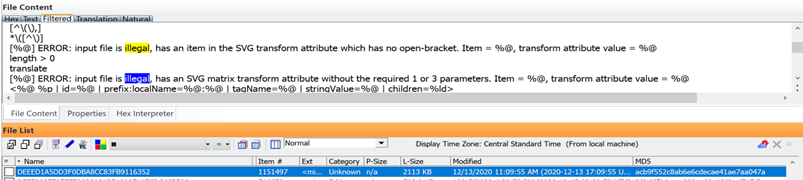
Injecting new data with new timestamp
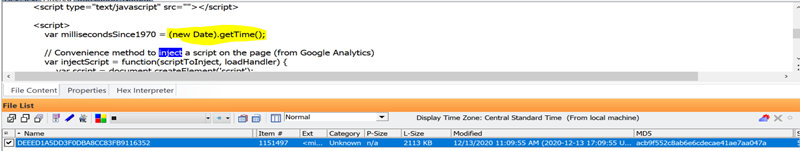
Code from the same file continued: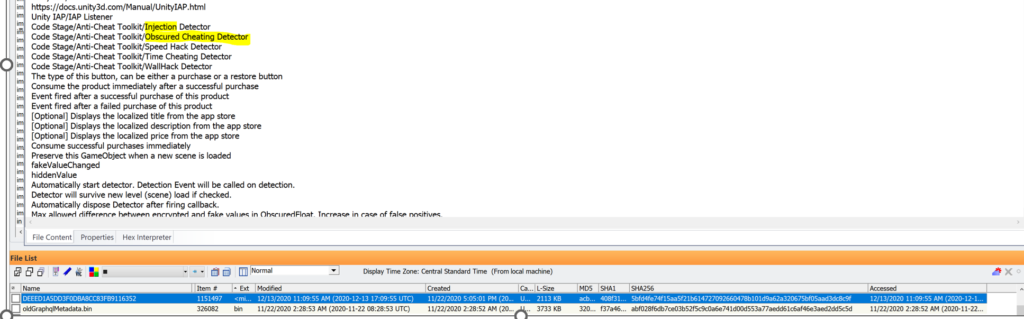
Page down in the same java file to see the statement run was “GetAssetBundleHash_Injected”

Page down again and you’ll notice that photographs appear to be injected back to the iPhone’s file system:
Page down again in the same file and there’s a text generator:

This particular iPhone Extraction was done in a different state over 2,000 miles away from the two cell phones in the case we just covered. The same “React Hot Loader” open source application is being used in place of the normal Apple IOS setup wizard and bundle:
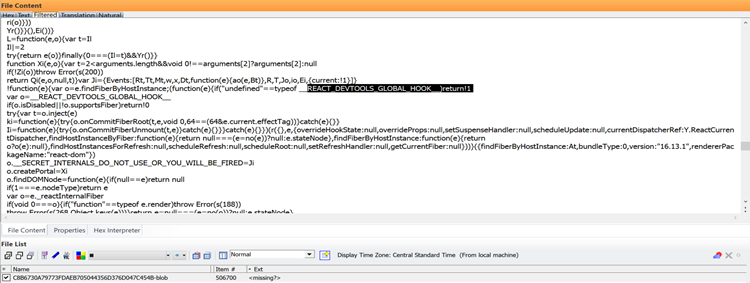
The same “Blueimp” date picker appears to be running on the device during the Hot loader’s setup wizard instead of the normal Apple IOS setup wizard: 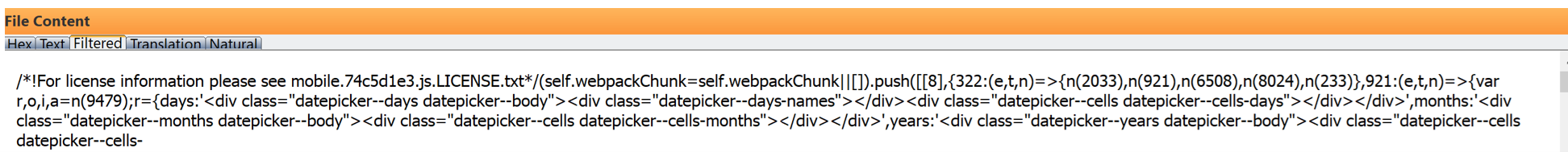
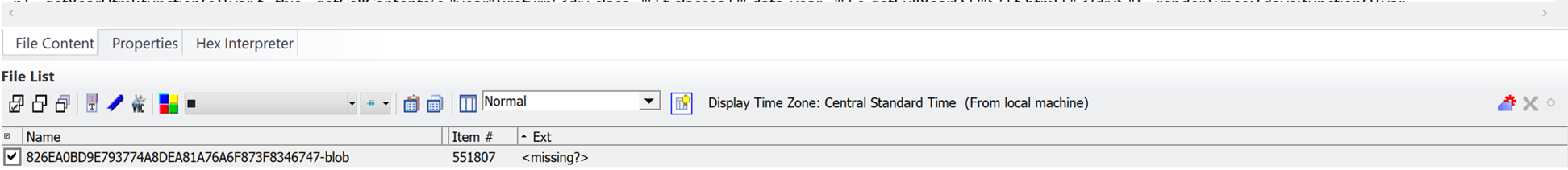
The same device extraction above indicates SQL statements where data is also inserted anddeleted after seizure. The code is not what you would normally see when the Apple IOS setup wizard creates the SMS.db sqlite database:
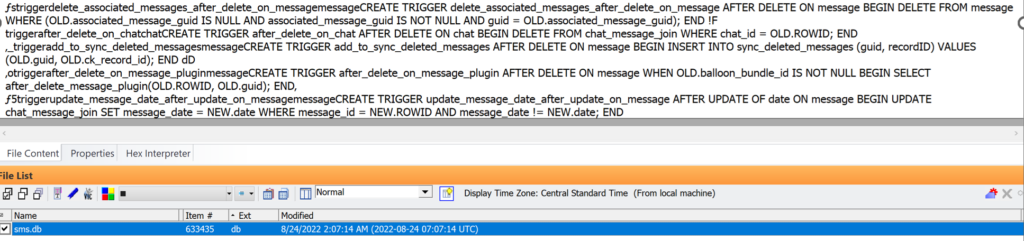
Here is the “FakeHash” statement on the same device when the write ahead log for the Photos.sqlite database indicates that a modified image was put back on the device after seizure:

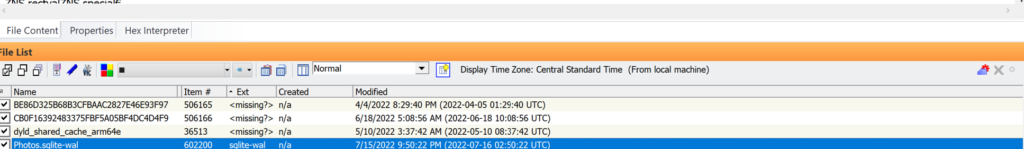 If you have access to .tracev3 files from a full file system extraction of an iPhone, these files can be very helpful in viewing the RTC time as opposed to the time set in IOS date and time settings. Here is an example of RTC time showing forward of the extraction date and time. This clock is integrated into the circuit board and does not lie: reference: https://en.wikipedia.org/wiki/Real-time_clock
If you have access to .tracev3 files from a full file system extraction of an iPhone, these files can be very helpful in viewing the RTC time as opposed to the time set in IOS date and time settings. Here is an example of RTC time showing forward of the extraction date and time. This clock is integrated into the circuit board and does not lie: reference: https://en.wikipedia.org/wiki/Real-time_clock
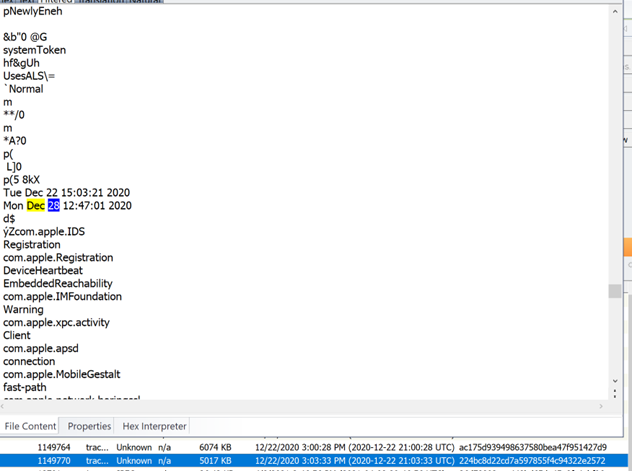
This tracev3 file shows the use of Darwin image validator after seizure: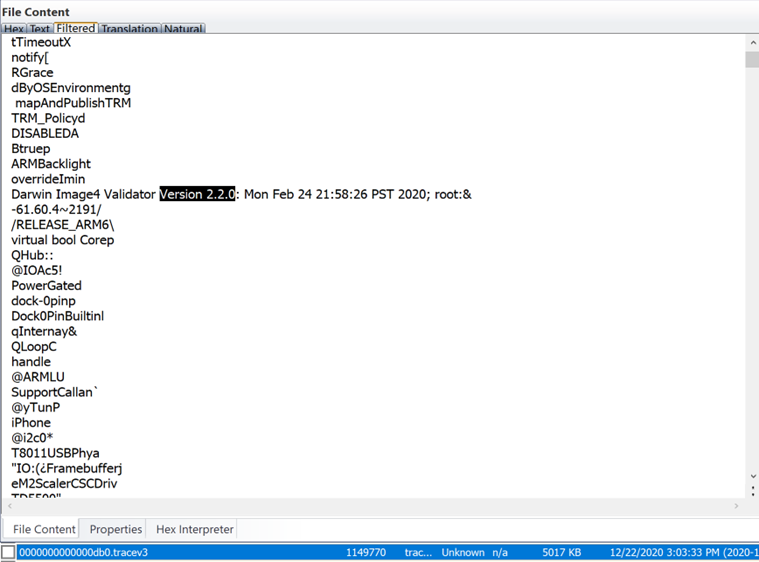
Scrolling down and there’s Photostream being used:
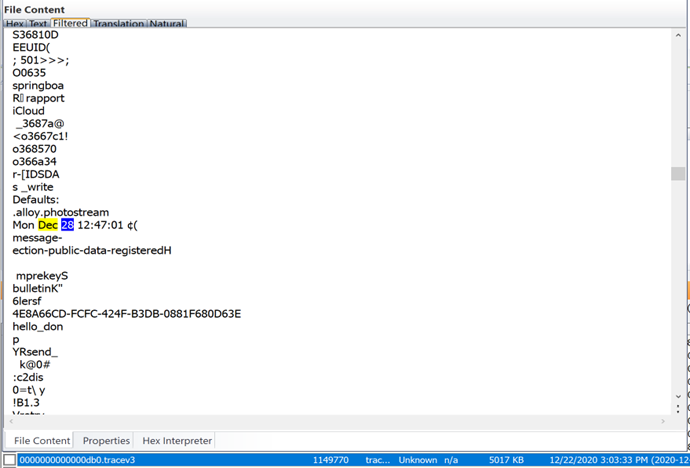
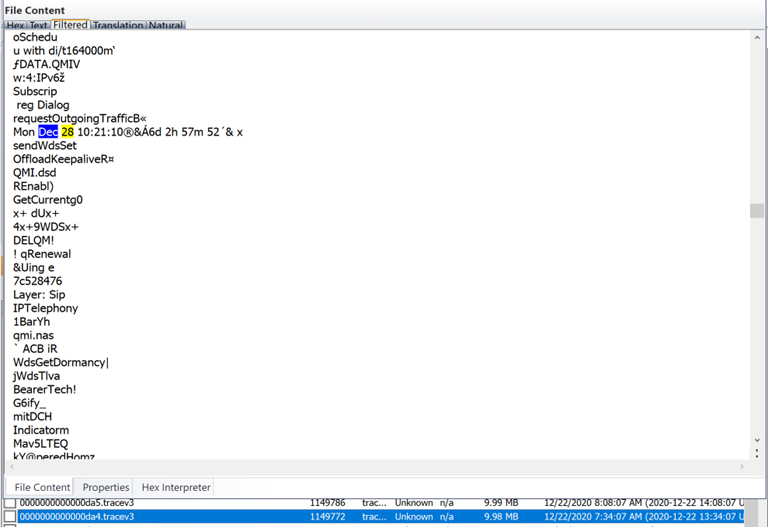
While this tracev3 file shows the device online when it’s supposed to be in airplane mode:
Another simple method to determine if there was manipulation of date and time settings is the powerlog databases. Here you my test iPhone as viewed through Cellebrite Physical Analyzer where the clock has not been manipulated: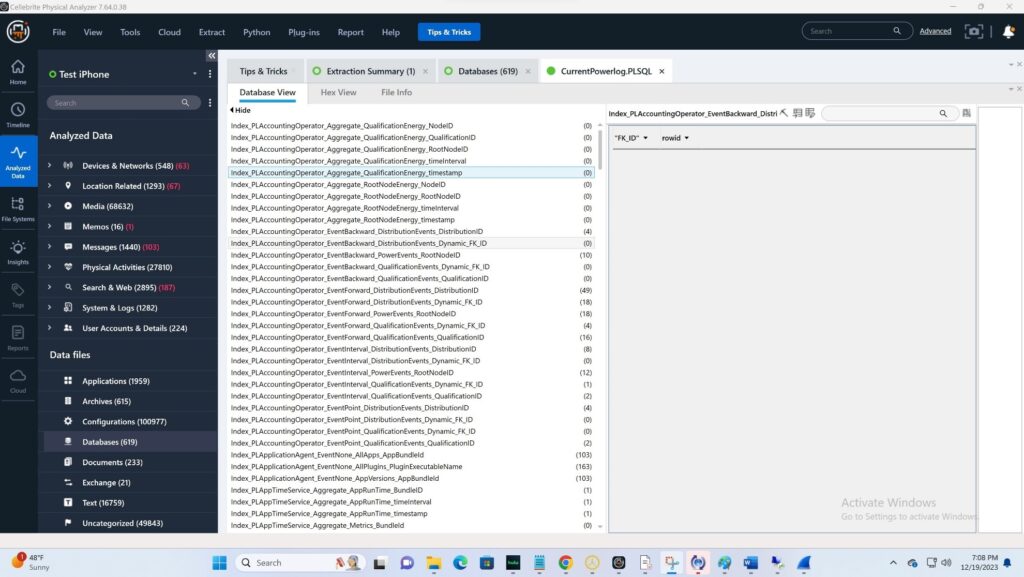
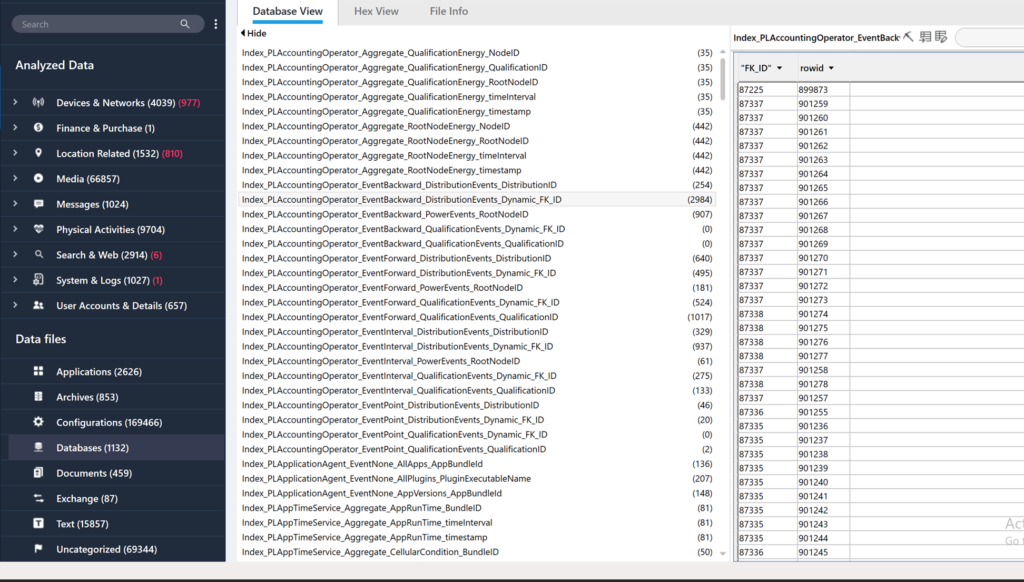
And here is the powerlog database as viewing from the SQLite viewer in Cellebrite where the clock was manipulated in a different case:
When running across java script for “Hot Loader”, “Global Hook”, and “Secret Internals” with the same warning, you’ll also see arguments for handling “Immutable” indexes. What does immutable mean in JavaScript?

What is Immutability in JavaScript? Immutability is the state where values are immutable (that is, not able to be changed). A value is immutable when altering it is impossible. Primitive data types are immutable, as we discussed above.
Reference: https://www.freecodecamp.org/news/mutability-vs-immutability-in-javascript/#:~:text=log(staff2)-,What%20is%20Immutability%20in%20JavaScript%3F,immutable%2C%20as%20we%20discussed%20above
The most disturbing thing about this suite of applications called “React Hot Loader” is that it has been around since 2016.
This is a different murder case in another city where the same open source Hot Loader was run on the phone after seizure:
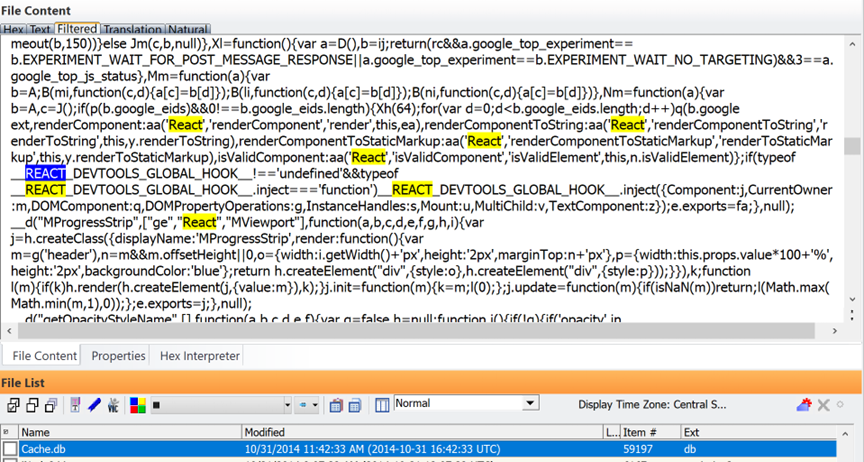
Here is another case in a different city going all the way back to 2016 where the same Hot loader suite of open source applications was run on the device after seizure:
I’ve been in the I.T. field since 1996, foremost as an MCSE and SQL DBA in the late 90’s then to computer forensics as they used to call it in 2002. I have spent most of my adult life studying applications and how they integrate with each other. I have always been a command line tech as well. Having used vb scripts in the early days as a network administrator, it’s easy to see things that make no sense in a security hierarchy of any operating system running on any computer, mobile device, server, router, or whatever.
My expertise is in the field of digital forensics and forensic data recovery including but not limited to flash memory storage of mobile devices, computer hard drives, DVR storage media, and RAID volumes. I have been a SQL database administrator involved in creating multiple custom web based applications for various law firms and the Alabama State Bar Foundation over the last 18 years. My first computer forensic project was in 2002.
I have been qualified by the State Bar when in 2019, I was hired to do an in-house project processing 22 mobile devices and computers to examine for the Bar. For this project, my .Net developer and I created a custom SQL based web application on the fly. This is so that the Bar Association could efficiently query email evidence. This allowed for the evidence to be shared online by two different law offices and the Bar Association itself. I’ve also been qualified as the court’s neutral expert in six different cases over the last 5 years, which were mostly commercial litigation cases and some wreck cases as well.
The reason that last paragraph is important is this. Most data stored on mobile devices whether they be IOS or Android operating systems are storing that data in SQLite databases. For example, If the photograph is too large to be blobbed into the Photos.sqlite database, there is always an EXIF transaction trail in some other related image database.
Please feel free to email any comments or feedback at scoker@cokerforensics.com
This article was written by:
Stephen D. Coker Jr.
Coker Forensics L.L.C.
Cellebrite Certified Physical Analyst (CCPA)
Cellebrite Certified Operator (CCO)
Certified Computer Forensics Examiner (CCFE)
Certified Mobile Forensics Examiner (CMFE)
Accessdata Certified Forensic Examiner (ACE)[/et_pb_text][/et_pb_column][et_pb_column type=”1_2″ _builder_version=”3.9″ parallax=”off” parallax_method=”on”][et_pb_text _builder_version=”3.9″][/et_pb_text][/et_pb_column][/et_pb_row][/et_pb_section]
